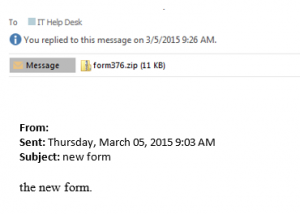
Email messages from compromised WCU faculty/staff accounts have recently been making the rounds, and these new phishing scams have affected WCU faculty, staff and students. In the most recent event which occurred on Thursday, March 5, the problem caused all on-campus email to be turned off for three hours and all day for faculty and staff who were infected by a Trojan virus as a result of the phishing scam.
Phishers will try and exploit the fact that you trust people that you know. When they compromise one account, they will often send messages to people who are in the address book of that person, hoping that the recipient will open the attachment because they trust the sender. If you receive a suspicious message from someone you know, as in the example below, follow up with them by phone or by text to make sure they sent it. If they didn’t, you should delete the message, and they should immediately change their password.
WCU has many security tools in place to help detect, block, and communicate known phishing attempts, but we also rely on the WCU community to be cautious when opening email messages.
One of the tools to assist you in determining whether an email is a phishing attempt is the required Information Security Awareness training, which covers this type of scenario. Information security awareness training is a requirement mandated through the adoption of ISO 27002 security standards by WCU and the entire UNC system. This mandatory training needs to be completed by all WCU faculty and staff by March 31, 2015, and it should take less than 30 minutes to complete.
The information security training videos can be viewed at your convenience. Only permanent employees will have access. Participants may log on by following these instructions:
• Go to Western’s Home Page (http://www.wcu.edu).
• Click once on the Blackboard link on the top bar.
• Use your WCU Active Directory network/email username and associated password to Login.
• Look for the course in which you are enrolled, click on Information Security Training – Year 2, and follow the instructions.
Additionally, to assist you in determining whether an email is a phishing attempt, here are seven questions to ask when browsing your inbox. The more red flags you see in an email, the more likely it is not legitimate:
1. Does the message contain general salutations and signatures? Most phishing attempts begin with generic phrases like “Greetings valued customer,” or “Dear account user.” Most legitimate companies, on the other hand, will include an intended recipient’s name in their correspondence. Another indication of phishing is a general signature at the end of the message, such as “The Email Team.”
2. Are the URLs legitimate? Emails containing Web links should always be questioned. One way to verify a link’s legitimacy is to hover your mouse cursor over embedded links and make sure the link uses encryption (look for the “s” in https://). Also, if a link in the text isn’t identical to the URL displayed when you hover the cursor over the link, that’s a sure sign it’s taking you somewhere you don’t want to go. Another best practice: open a new browser window and visit a site directly by pasting in its Web address, or URL, rather than simply clicking the link in an email and going wherever it takes you.
3. Is the sender requesting personal information? Providing personal information through email or by phone in response to an unsolicited request is always a bad idea. Messages soliciting passwords, Social Security numbers and other personal information are scams.
4. Is the email asking you to take immediate action? Hackers want you to respond without thinking. Phishing emails might even claim a response is required within a short timeframe because your account has been compromised. Watch out for language directing you to update an account, download an attachment, visit a website, provide personal information, etc.
5. Does the message contain suspicious attachments? Opening attachments can cause automatic malware downloads or lead to compromised personal information. High-risk attachment file types include: .exe, .scr, .zip, .com, and .bat.
6. Is the email making promises that seem too good to be true? Then they probably are. Any message offering to put money in your bank account with a single click is a scam.
7. Are there misspellings or typos? An email from a legitimate organization should be well-written. Grammar and spelling mistakes are red flags.
What to do if you receive a phishing email: When you see suspicious email in your WCU inbox, report it to ithelp@wcu.edu with the original email attached to preserve its header information. Doing so helps IT division staff review the message and advise if it is legitimate. IT staff also can take measures to block fraudulent websites.
To attach an email in Windows using Outlook, create a new message and choose Attach Item from the dropdown list on the message menu bar. Then select Outlook item and attach the email in question. On a Mac, right-click or control-click on the suspicious message and choose Forward Special and As Attachment from the dropdown list.
Please contact the IT Help Desk for any questions or concerns.
IT Help Desk
help.wcu.edu
227-7487 (local)
866-928-7487 (toll free)
Available weekdays 7:30 a.m.-6:30 p.m. ET
As a reminder, IT will never ask you to confirm account information, such as username and password, through email.