
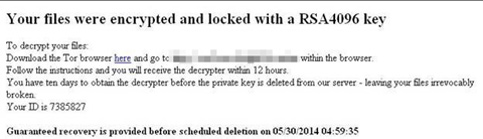
- What Is it? Malicious software (Malware) delivered to your computer which prevents you from accessing your files most often by encrypting them. To get access to your files again you are instructed to pay a ransom to get the key to unencrypt them (see below):
- How can I get this on my computer? Most likely through Phishing Emails with infected attachments or links to a website hosting the malware exploit kit. The malware can also be secretly downloaded by browsing to websites that are infected.
- How can I prevent it? (see video)
- Make backups of critical data to removable storage (flash drives, CD-ROMs) or your Microsoft OneDrive storage.
- limit web surfing to reputable web sites
- avoid opening e-mails and attachments received from unknown individuals or are otherwise suspicious in nature
- do not install shareware, freeware, commercial, or personally developed software without authorization
- Also, use the “suspicious hover” technique – float mouse cursor over email links, wait for pop-up, verify link matches link shown
- Should I pay? The FBI does not advocate paying a ransom to an adversary. Paying a ransom does not guarantee an organization will regain access to their data. In fact, some individuals or organizations were never provided with decryption keys after paying a ransom.
- What do I do if it happens to me? First, do not pay the ransom. Second:
Contact the IT Help Desk
Monday-Friday, 7:30 a.m – 6:30 p.m.
Closed weekends and university holidays
Call: 227-7487 or 866-928-7487 (toll free)
E-mail: ithelp@wcu.edu
Log in: Online Help Desk/IT Self-Service http://help.wcu.edu
